We are Living in Exponential Times

We are living in exponential times. While that fact makes it exceedingly exciting to be alive right now, it also comes with a lot of procurement related issues. Let’s examine a few facts, and see if you can realise where I am going with this:
- In 1984, there were 1,000 internet capable devices.
- By 1992, there were 1,000,000.
- In 2008, there were 1,000,000,000.
- Today it is estimated at 30,000,000,000.
- Last year, 4 exabytes (4.0 x 10^18) of unique information was generated, which is more than the previous 5,000 years in total!
- It is estimated that there will be 70 billion connected devices by 2025.
- NTT Japan has successfully tested a fiber optic cable that pushes 14 trillion bits per second down a single strand of fiber
- Technical obsolescence is accelerated with technologies becoming obsolesced in as little as 3 years!
The Exponential Risk in Your Tail Spend
Let’s talk about third-party risk management. In procurement we need to focus on getting the correct supplier/provider/adviser at the best total cost, delivering the right level of quality and service levels.
To most people, this means that we are living in exponential times. But to a procurement person it means “oh no, I need to look at all of my supplier relationships because of the possible threat of risk.” The issue with this logic is we don’t know what we don’t know. And that means we have probably done little to no research/cyber security/risk assessment on our tail spend, let alone on every supplier in our critical spend.
Most companies have entered into multi-year agreements with their critical spend suppliers. This is in an effort to secure the best total cost of ownership and allow ample time for their suppliers to retool, ramp up and to get to know them in order to meet their service and quality requirements.
Therefore, despite quarterly business reviews (QBRs), it can possibly be as long as one to 10 years since that contract and relationship has been assessed (if ever) for real third-party risks.
Getting to Grips with your Supply Chain
I speak with CPOs on a daily basis and every one of them admits that they do not have a perfect grasp of their third parties, let alone their fourth-, fifth- or sixth-level parties. When was the last time you asked a supplier (especially in the tail) if they ever subcontract? Or whether their third parties, or fourth, have been reviewed for cyber risk? Or any risk at all for that matter?
Do you know whether your fourth parties are using human slavery? If every device is updated for the latest virus check? Whether employees are charging their phones through their devices, or if they are permitted to insert USBs into their computers from an unknown source?
How do we know if our fourth-level parties have a proof of mining to avoid conflict minerals? When was the last time we even checked our own staff for complying with strong cybersecurity norms?
The Cyber Risks Within Your Organisation
Just recently at a convention for hackers, cables that looked like Lightning cables were modified with extra hardware that gave hackers remote access to devices. Here’s how they work:
“O.MG cables are indistinguishable from the real thing, and they even come with the iconic adhesive binding rings you’ll find wrapped around new Apple cables. The [modified] cables act normally, too, letting you charge your devices via USB or transfer files from your iOS devices.
Neither your PC nor your connected devices will ever notice that anything is amiss. Short of dissecting the cable to look for the extra hardware, the only way to detect that you’re using an O.MG cable is when you realize, after the fact, that your device was exploited.
And even if you happen to catch an attacker running a terminal window on your PC remotely, O.MG cables include a kill switch that disables the implanted hardware, thus destroying any possibility to track down the attack’s origins.”
‘These Dummy iOS Lightning Cables Let Hackers Remotely Access Your Devices’, Lifehacker, August 2019
Secure Apps?
Apple would have you believe that your iPhone is very secure, until you add your first app. For example, when traveling recently I downloaded an app to play Dominoes (the game, not the pizza). This is seemingly innocent, but since I was on a long flight, I actually read the privacy information.
Check out some of the following extracts from the Terms & Conditions and Privacy Information:
- FM GAMES App is a gaming application that may utilise your personal data. You also consent to FM GAMES’s cookie policies, as described herein.
- Types Of Data We Collect: We collect personal data and non-personal data about you.
- Location and Distance Information: When you use the FM GAMES App, we will collect your location to determine your distance from other users (“Distance Information”) through the GPS, Wi-Fi, and/or cellular technology in your Device. Your last known location may be stored for the purpose of calculating Distance Information between you and other users.
- Messages: When you send a message we may retain the message for archival purposes or as otherwise allowed by law.
- Purchases: We collect information necessary to complete purchases. This may include, among other things, your name, credit card information, billing information, address, telephone number, and email address.
- Third Party Tracking Companies: We may share your hashed Device ID, Profile Information, Distance Information, and demographic information with our advertising and analytics partners. These third parties may also collect information directly from you as described in this Privacy Policy.
- Third Party Service Providers: We may share your Personal Data with third party service providers
When I tried to turn off location services, this was not allowed, so I discarded the app. If this is the case with a gaming app for my phone, can you imagine the angst my home screen caused our IT folks?
Would you know if you had been hacked?
If I charge my phone through my computer, imagine what I am opening up for hackers to get to? How many of you reading this are using public Wi-Fi? What about Starbucks, or at the airport? Many of us will pass through at least one on the way to the Procurious Big Ideas event.
Did you connect to the seemingly innocent Wi-Fi? Would you know if you were hacked? If you haven’t heard about the reporter whose email was hacked on an airplane while using the airline app while working on a story about the FBI and Apple, take the time to do so.
The hacker read nearly everyone’s email on the plane. They then pulled the reporter aside when they landed to discuss the security, or lack thereof, of his phone while using public Wi-Fi, even if was at 35,000 feet.
The Fallability of Passwords
If this isn’t enough, consider what anyone can do with your passwords. Take for example my login for Amazon. If you were able to see my screen while I was logging in, this is what you could do.
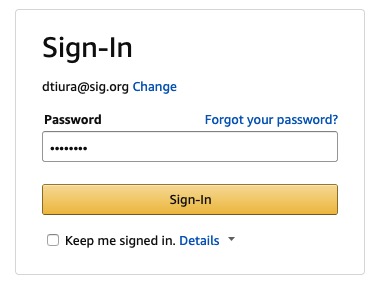
Then, if in Chrome, right click and click on Inspect.
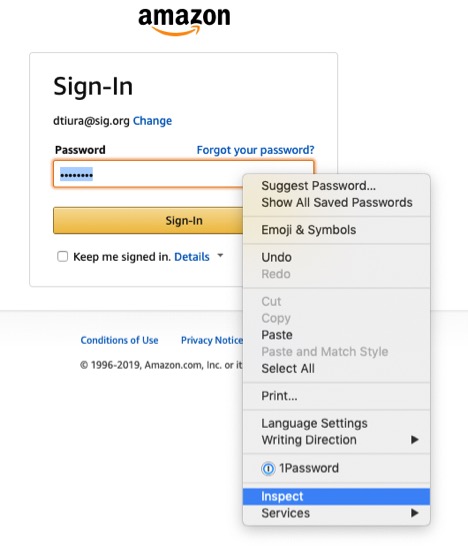
By merely highlighting the password and writing the word “text,” you will see my password. It is that easy if someone is “looking at your email” as you are logged in.
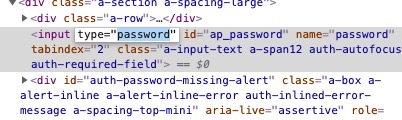
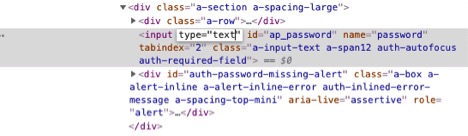
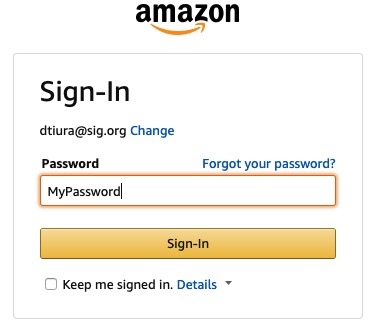
So, there you go. This is my Amazon password and I have now changed it since I wrote this post (but don’t tell my kids). This is the most basic level of cyber protection you can get, but even at a personal level with my own “research,” we are so out of our league, especially when dealing with technology obsolescence.
In the era of BYOD (bring your own device) who knows what your staff is exposing your company to. If we take this one level further to our third parties, who out there is doing the exact same thing and exposing their company to the same risks I just showed you?
So, while we are going to discuss third-party risk management in my session at The Big Ideas Summit, this is just the icing on the cake. If I am just one of the hundreds of contractors, imagine what damage I could be doing to your risk profile.
The Art of Third-Party Risk Management
So, the long and short of it, we are living in exponential times and it is time we paid clear attention to all of our third-party relationships (and their third parties, etc.) along our supply chains or we are destined to be in for a large risk event. It isn’t a matter of if, but when it will happen. If technology obsolescence is happening faster all the time, then we need to stay educated and alert, not paranoid.
To overcome these obstacles, we need to have an effective third-party relationship management and framework. Successful third-party management programs should focus on the four cornerstones approach: contract and performance management, risk management, financial management and communication management. The risk aspect of the relationship framework needs to be addressed for both critical and non-vendor relationships, along with non-critical vendors.
I recently took SIG University’s Third Party Risk Management Certification Program and was amazed to learn how much risk we are exposed to within our contracts and the need for a strong third-party relationship framework with a focus on risk. For a framework to be successful, it must have strong governance and approved by senior management.
As a result of the 2008 financial crisis, there has been a renewed focus on the role of board of directors, the composition of the board, capabilities, accountabilities, and responsibilities for prudent acceptance and management of risk. This renewed focus has made it much easier to focus on third-party risk and to get strong governance in place to mitigate risks.
The most important lesson to leave you with is that third-party risk management is an art, not a perfect science. Having a framework in place to address and mitigate risk, escalate issues and seek resolution is the key to making strategic procurement decisions.
Learn more about procurement’s role in managing third-party risk by attending Dawn’s session at the Procurious Big Ideas Summit Chicago 2019 on Wednesday, September 18. If you can’t be in the room, there’s still time to register as a Digital Delegate. Find out more and sign up today!
About the Author
Dawn Tiura is the CEO and President of SIG, SIG University and Future of Sourcing and has over 26 years’ leadership experience, with the past 22 years focused on the sourcing and outsourcing industry.
In 2007, Dawn joined SIG as CEO, but has been active in SIG as a speaker and trusted advisor since 1999, bringing the latest developments in sourcing and outsourcing to SIG members. Prior to joining SIG, Dawn held leadership positions as CEO of Denali Group and before that as a partner in a CPA firm. Dawn is actively involved on a number of boards promoting civic, health and children’s issues in the Jacksonville, Florida area.
She is a licensed CPA and has a BA from the University of Michigan and an MS in taxation from Golden Gate University. Dawn brings to SIG a culture of brainstorming and internal innovation.